Everyone is paying attention to cloud computing and cybersecurity. As businesses shift into the modern digital landscape, everyone must now safeguard sensitive data with cloud-based security. Proactive strategies that can protect digital assets have become a staple of cybersecurity services, ours included.
Let's explore everything you need to know about cloud security, along with some practical techniques you can use to secure your infrastructure.
What is cloud computing cybersecurity?
Cloud security refers to a set of cloud-based security technologies, strategies, and best practices. Since the cloud offers new avenues for providers (IaaS, PaaS, or SaaS) to deliver resources and services, it also presents a new attack horizon for criminals. As a discipline, cloud security covers the wide range of security considerations that defend against such threats.
Cloud security also depicts the shared responsibility held by all involved parties. As companies use the cloud scale, the risk of cyber threats (breaches, unauthorized access, service disruptions) increases. All service provider types and customer organizations shoulder that security risk at varying levels, best shown in the shared responsibility matrix below.
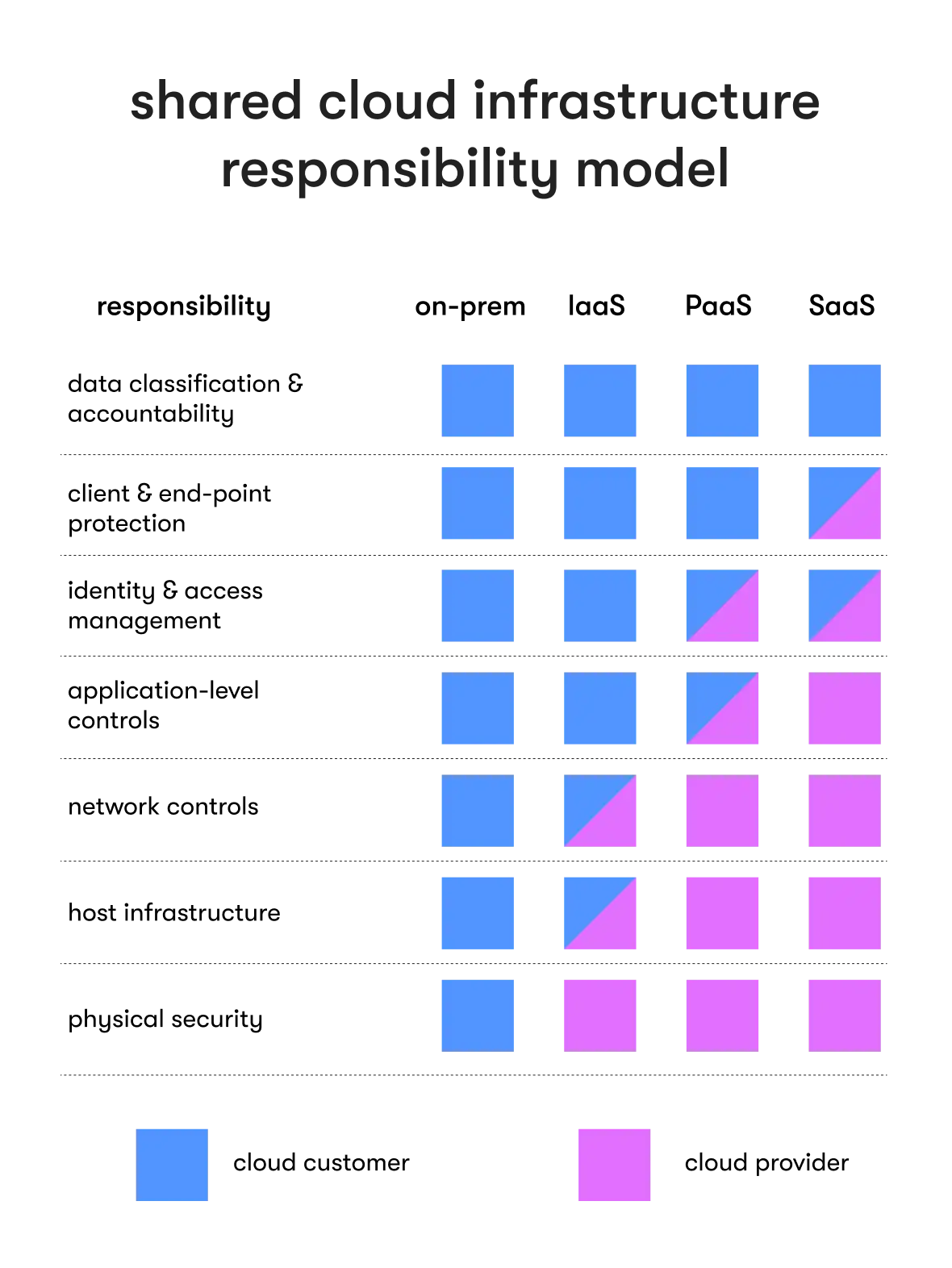
Together, everyone can maintain digital integrity with cloud-based security measures. And when the underlying cloud computing environment is secure, the benefits of the cloud become accessible.
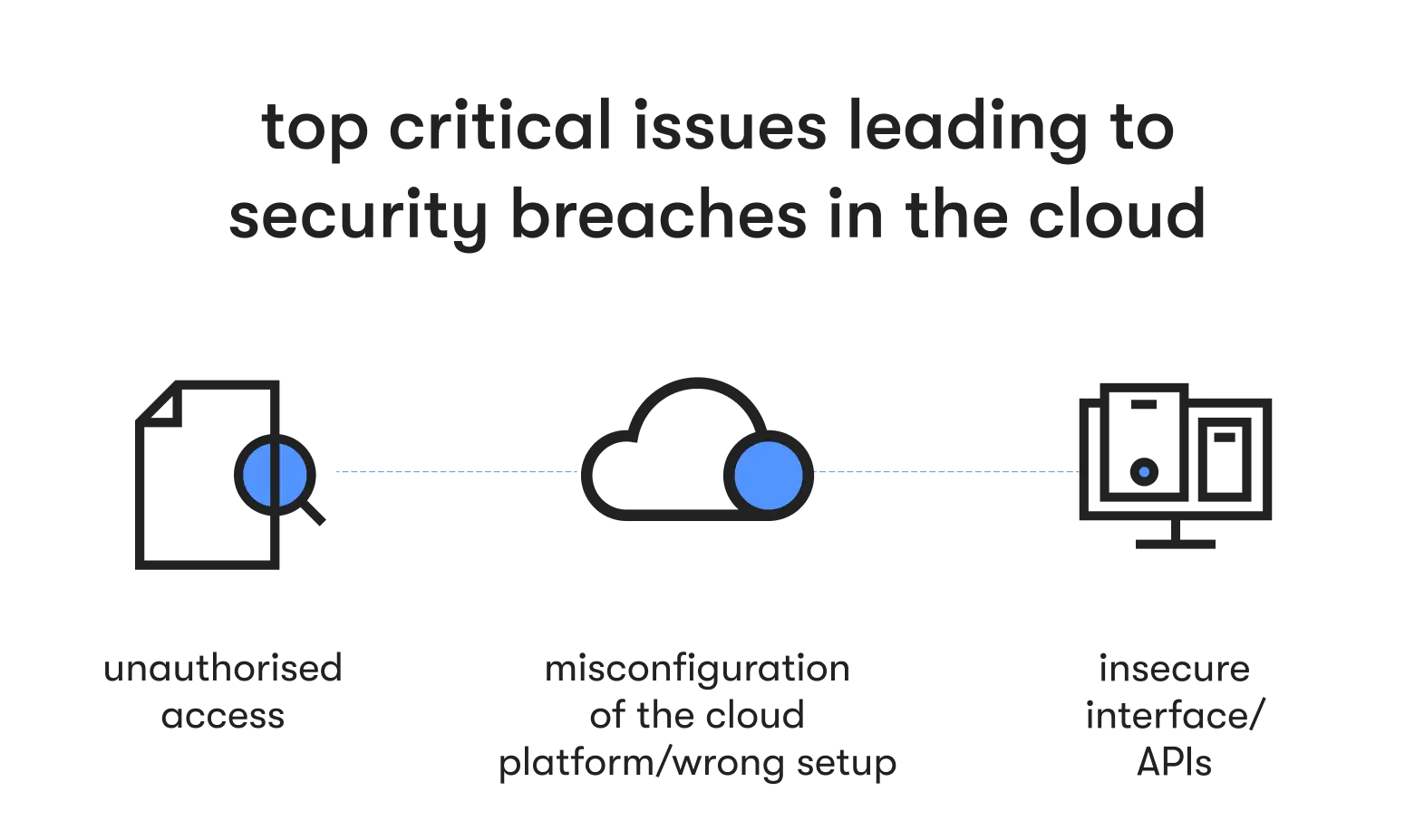
Top reasons for cloud security breaches
Unfortunately, many organizations have poorly configured security measures. Cloud security is complex and cyber threats are becoming more sophisticated. Those who are unprepared can fall victim to the following:
- Lack of visibility: If an organization cannot monitor user activity or network traffic, it’s hard for security teams to identify security breaches. Moreover, limited visibility eliminates all possible proactive response strategies, leaving companies exposed to emerging threats.
- Dependencies: The cloud demands reliance on a host and extra third-party services. That creates a collateral risk, as data breaches can occur at the provider level. Improperly vetted service providers or applications are weak points that criminals attack.
- Inadequate access controls: The cloud is expansive, and that makes user restrictions a challenge. Internal employees now pose a risk as an insider threat. Weak user credentials are susceptible to brute-force attacks or phishing scams, and failure to manage access privileges can result in unauthorized access.
- Misfigured security: Open ports, a lack of encryption, or incorrect network setup all act as vulnerabilities that a cybercriminal can exploit in the cloud.
Cybersecurity implications of cloud computing for your business
A lot of the cybersecurity cloud computing problems stem from resistance to change. Before, cybersecurity involved on-premise, virtually protected environments controlled by in-house security teams. Now, the cloud keeps all data online and in the hands of shared external providers. It’s a new paradigm that reframes what cybersecurity means to your organization.
For example, data security and confidentiality practices will evolve. Sensitive data is no longer held within your company, instead resting with a third-party service provider. As a result, encryption and access control take on greater importance.
Or consider your approach to identity management. Many users will attempt to access data stored in the cloud, which exposes you to attacks related to compromised passwords, insider threats, and phishing scams. Permissions, authorization controls, and authentication are now crucial elements of your cybersecurity.
Data loss also becomes integral to your business IT systems in cloud computing. Attacks, breaches, and system malfunctions all cause downtime that can impact your business operations. Disaster recovery plans and robust backup strategies will become key aspects of your security policies.
Of course, compliance requirements will change as well. Data protection and privacy laws expanded as cyberattacks became more sophisticated (the best example is the EU’s General Data Protection Regulation). You now have a legal responsibility to your customers that includes threat detection, monitoring, and employee training. Different industries will have security protocols that will alter the operation of your business as you move into the cloud.
Naturally, many IT leaders and security teams protested against such changes. Cybersecurity professionals wisely avoid unnecessary risk, and the cloud is far more complex to secure than legacy systems. Many organizations delayed adopting cloud innovations, for example with cybersecurity in banking, where banks hesitated to upgrade.
But as the number of businesses that migrate to the cloud increases, such hesitancy leads to technical debt, where choices for suboptimal security solutions compromise overall security. Quick fixes and patches overstretch security teams, and the lack of innovation increases security risk as outdated systems cannot defend against modern cloud-based attacks.
In short, if you don’t shift to the cloud and adopt comprehensive cloud security now, you risk the fallout from a breach. That includes losing customers, a negative impact on your brand, and direct financial losses. You need to focus on the cybersecurity implications of cloud computing, or you will fall behind.
READY TO FORTIFY YOUR CLOUD INFRASTRUCTURE AGAINST EVOLVING THREATS?
Partner with EPAM Startups & SMBs and benefit from our cybersecurity solutions.
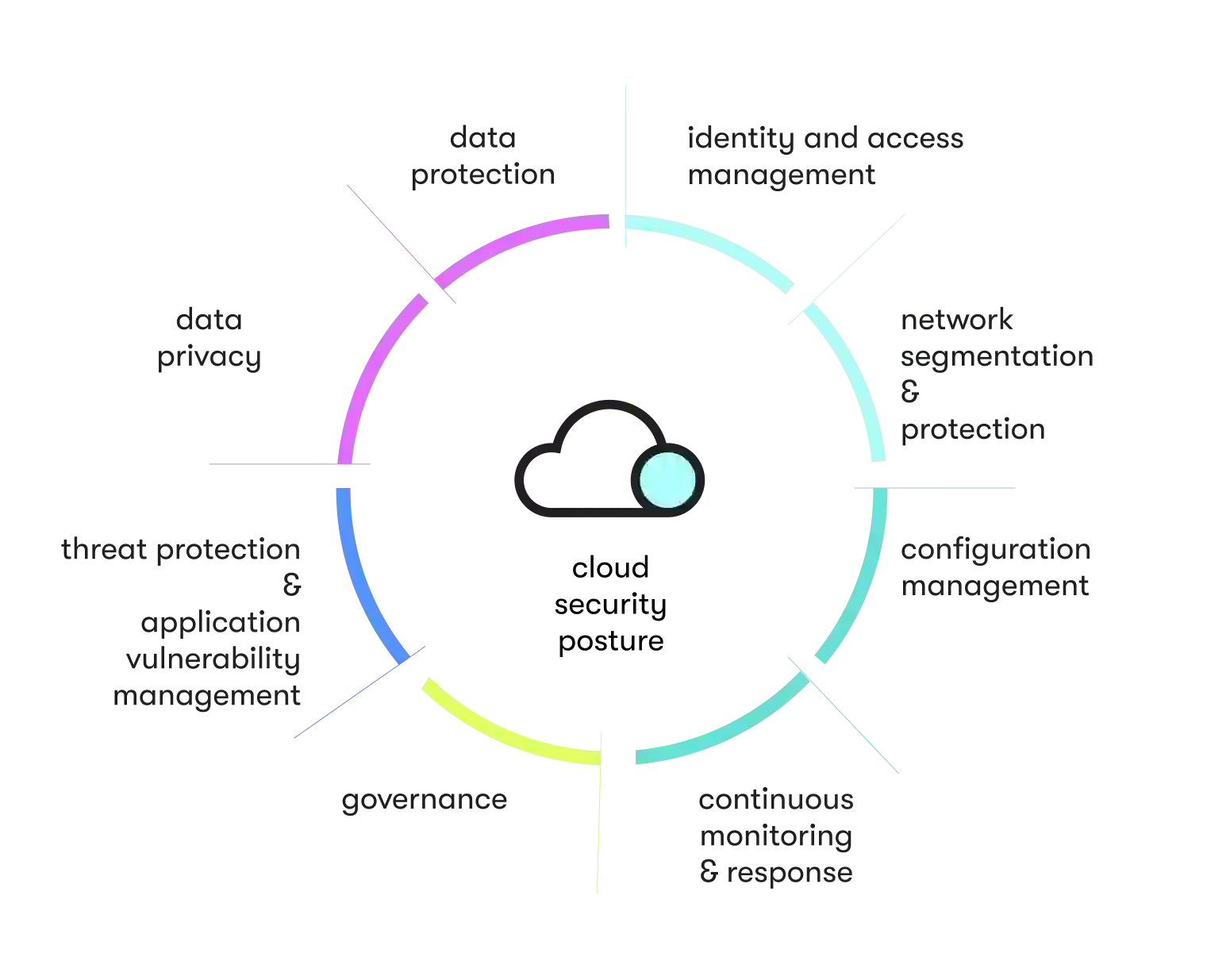
8 essential components of the holistic cloud computing cybersecurity
Luckily, cloud security and cybersecurity services have greatly expanded. Digital solutions and technologies allow you to build a cloud security posture that protects your assets.
The ideal method for safeguarding your organization is the holistic approach. The holistic approach to cloud computing security is a set of security principles designed to address your entire ecosystem. When you view your cloud security as an embedded element in your organization, you can better defend against known vulnerabilities. Use the following eight essential components to help frame a resilient cloud security posture:
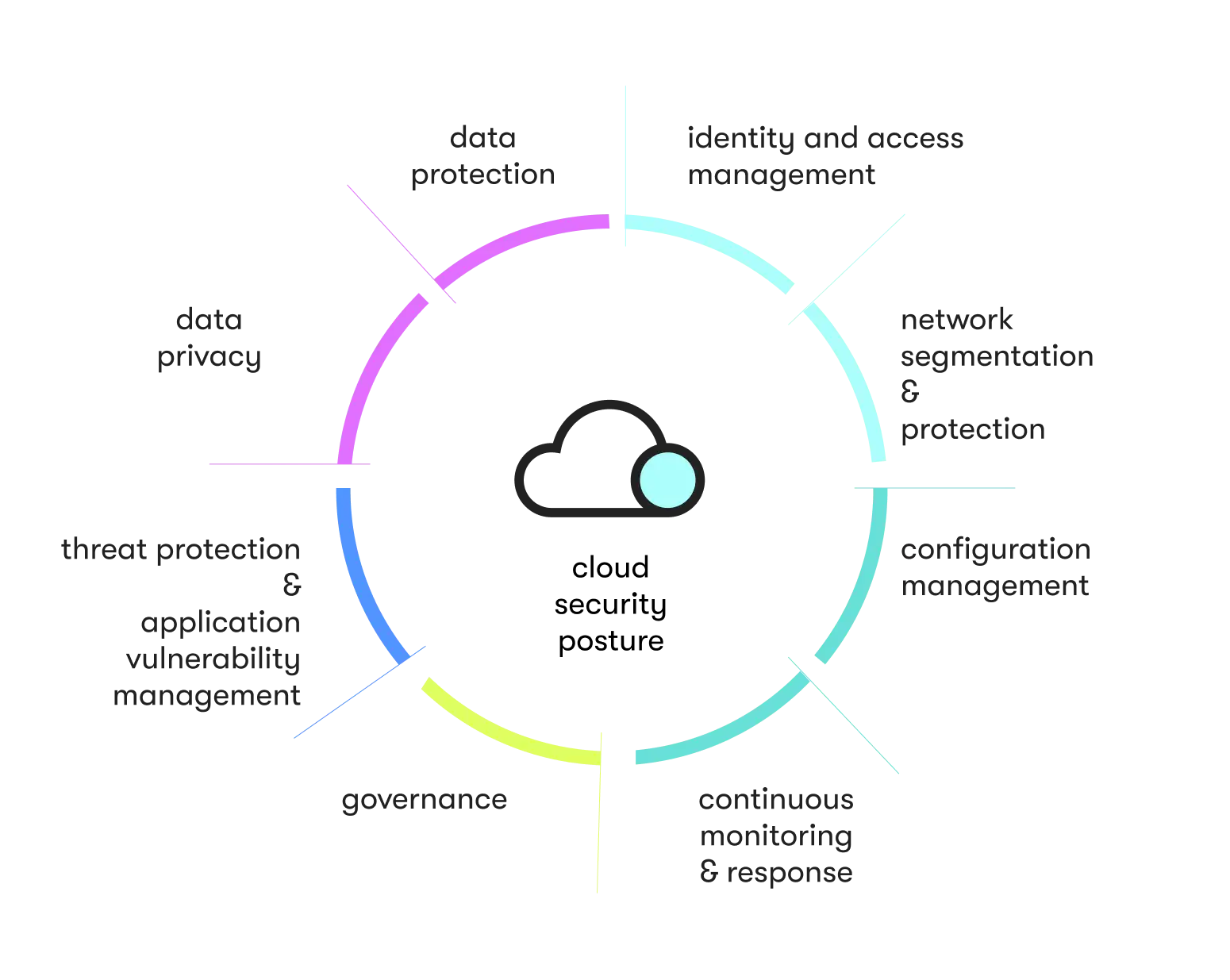
Governance
Focus on comprehensive security policies. Governance policies should outline in clear terms proper cloud usage within your business. That includes data protection, incident response, and employee training. Governance documents create a visible security framework that provides the base of your cybersecurity cloud computing strategy.
Configuration management
Consider the configurations of your hardware and software. Mismanaged elements fail to communicate, and that results in security vulnerabilities. When possible, automate various configuration states in a centralized platform. Proper configuration is the foundation of your defense.
Identity management
Focus on access restrictions. Only those with proper clearance should be able to enter your cloud. To manage permissions, assign strict access rights based on job function and the priority level of the data. The quality of your cloud security is only as strong as its weakest link, so use access controls to shore up a common point of attack.
Data protection and privacy
Invest in data protection solutions that can safeguard your data. The strength of your defense posture depends on the quality of the tools you use. Common examples include encryption, deletion policies, and cloud workload protection.
Threat intelligence and prevention
Emphasize threat intelligence to proactively defend against emerging threats. The more up to date you are about emerging threats and attack behaviors, the stronger your defenses. Well-defined procedures that detect and respond to breaches should be a crucial element of your cloud security strategy.
Network security
Consider your cloud network security for all traffic and communications within the cloud. To protect that infrastructure, set up a next-gen web application firewall (WAF), intrusion monitoring systems, and virtual private networks (VPNs). Such efforts help mitigate damage when cybercriminals gain access.
Continuous monitoring and vulnerability management
Maintain rigorous vulnerability testing. Discovery should occur on an ongoing basis and remain a crucial pillar of your security posture. Not only will unified visibility across multi-cloud environments help you locate misconfigurations, but active monitoring can detect threats with far less time (and with breaches, time is of the essence).
Internal awareness
Teach all stakeholders about the importance of a secure cloud environment. Training programs should cover password management, social engineering, and safe data handling. Regular awareness campaigns and strict adherence to least privilege operations help secure the cloud at its endpoints (devices, users, employees).
TALK TO OUR SECURITY EXPERTS
Get a free consultation on cybersecurity protection for your business.
How to get started with securing your cloud infrastructure
EPAM Startups & SMBs offers a range of cloud network and cybersecurity services, including secure cloud solutions for banks. Our certified experts have developed cloud security implementation strategies with a proven track record of success. If you want to protect your cloud and data ecosystem, here are some steps to get you started:
1. Start with cloud infrastructure assessment
Evaluate your current cloud infrastructure. Create a complete inventory of your cloud assets (virtual machines, databases, applications, etc.) and how they interact and communicate. With that information, you can better configure your security controls (firewalls, encryption settings, logging mechanisms) and perform tasks such as compliance evaluation.
2. Create a cloud security roadmap
Next, develop your security policies and objectives. Clearly define your expected outcomes. Having a core vision for your security posture will help classify the roles and responsibilities of your security teams as well as outline how your organization will achieve data privacy, confidentiality, and integrity. Lastly, engage in both a cloud host and cybersecurity services provider vetting. Use your cloud documentation to select reputable providers that meet your security requirements.
Establish strong identity and access management (IAM)
With a clear roadmap, establish basic IAM best practices that securely control user access. That includes Role-based access control (RBAC) to assign access permissions and privileged access management (PAM) to monitor privileges for escalated accounts. You can also invest in additional safeguards like segmenting or multi-factor authentications to limit lateral movements by hackers.
Implement security information and event management (SIEM)
With access restrictions all mapped, your security teams can safely develop incident protocols. Integrate SIEM solutions to analyze security events in real time. Centralized logging will give you greater visibility over your entire ecosystem, and SIEM can then use that data to detect anomalies or suspicious behavior as part of information security protection. You can also use intrusion detection and prevention systems to block potential breaches and generate alerts. Afterward, your incident response capabilities will drastically improve.
Invest in robust security controls
Now that you have a complex cloud security framework, integrate data protection solutions and SaaS security services that can further improve your data protection capabilities. For example, encrypt all data with Transport Layer Security (TLS) and Secure Sockets Layer (SSL). Configure all firewalls, and allow security professionals to isolate your cloud resources for better network segmentation. Install robust data recovery and backups. Review your Domain Name System (DNS) and Dynamic Host Configuration Protocol (DHCP) to protect against DNS-related attacks. Use the available services to bolster your security defenses.
Monitor and test
With a robust defensive posture, be proactive with non-stop monitoring tools and routine security assessments. Cyber threats continue to evolve, but regular testing can keep you ahead of emerging threats. Engage in vulnerability patching and employ threat intelligence to further ensure operational continuity. Red team and blue team exercises are of great assistance in this stage. The more weaknesses you discover and fix, the safer your cloud environment becomes.
Shift security left in your CI/CD
Lastly, continuously improve by embedding your cloud security directly into the software development lifecycle. That means involving all security considerations from the initial planning phases. Automate all security tests (static application security testing and dynamic application security testing) so that all security adjusts as coding changes. CI/CD also promotes cross-collaboration between cloud development and security teams for faster and more secure software delivery.
Conclusion
If you want to capture the benefits of the cloud, your cybersecurity posture must improve.
But robust cloud security is complex. Even with the growth of cloud computing and cybersecurity services, misconfiguration still occurs — and cyber threats continue to evolve. Staying ahead of the curve can present a massive hurdle for organizations that currently hold high levels of tech debt.
If you need help protecting your cloud assets, consider connecting with a tech partner like EPAM Startups & SMBs. Security professionals can help you elevate your infrastructure into a compliant security posture. The experts can help you efficiently address cloud-based security issues that arise as you shift into cloud environments.
DO YOU NEED EXPERT ASSISTANCE WITH YOUR CYBERSECURITY POSTURE?
Explore comprehensive cybersecurity services delivered by the experts at EPAM Startups & SMBs.

Expert digital communicator and editor providing insights and research-based guides for technology buyers globally.
Expert digital communicator and editor providing insights and research-based guides for technology buyers globally.
Explore our Editorial Policy to learn more about our standards for content creation.
read more