Our editorial team is continuing a cybersecurity-related series of blog posts. In the article you’re about to read, you will learn about cybersecurity service providers (CSSP), cybersecurity as a service, and how SMBs and startups can get started with CSSPs to prioritize their security.
What is a cybersecurity service provider (CSSP)?
Cybersecurity is a domain of <wbr><wbr>information technology that deals with protecting networks and devices from malicious attacks or unauthorized access.
Now let’s find out what the CSSP meaning is. A cybersecurity service provider (CSSP) is an entity that offers cybersecurity services to businesses. They are also called managed security services providers (MSSPs), meaning they provide outsourced monitoring, security management, and cybersecurity solutions.
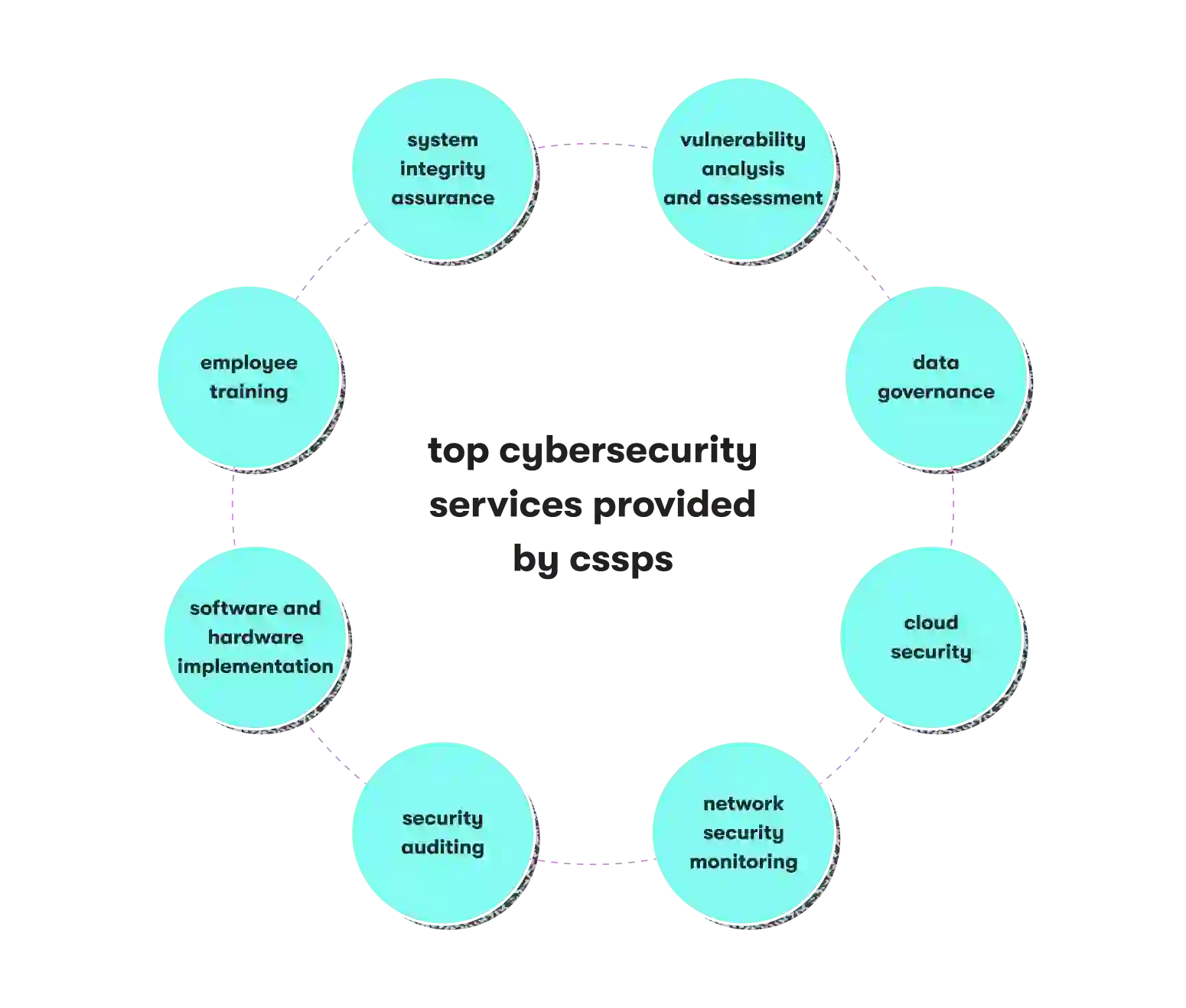
What does a typical cybersecurity services list include?
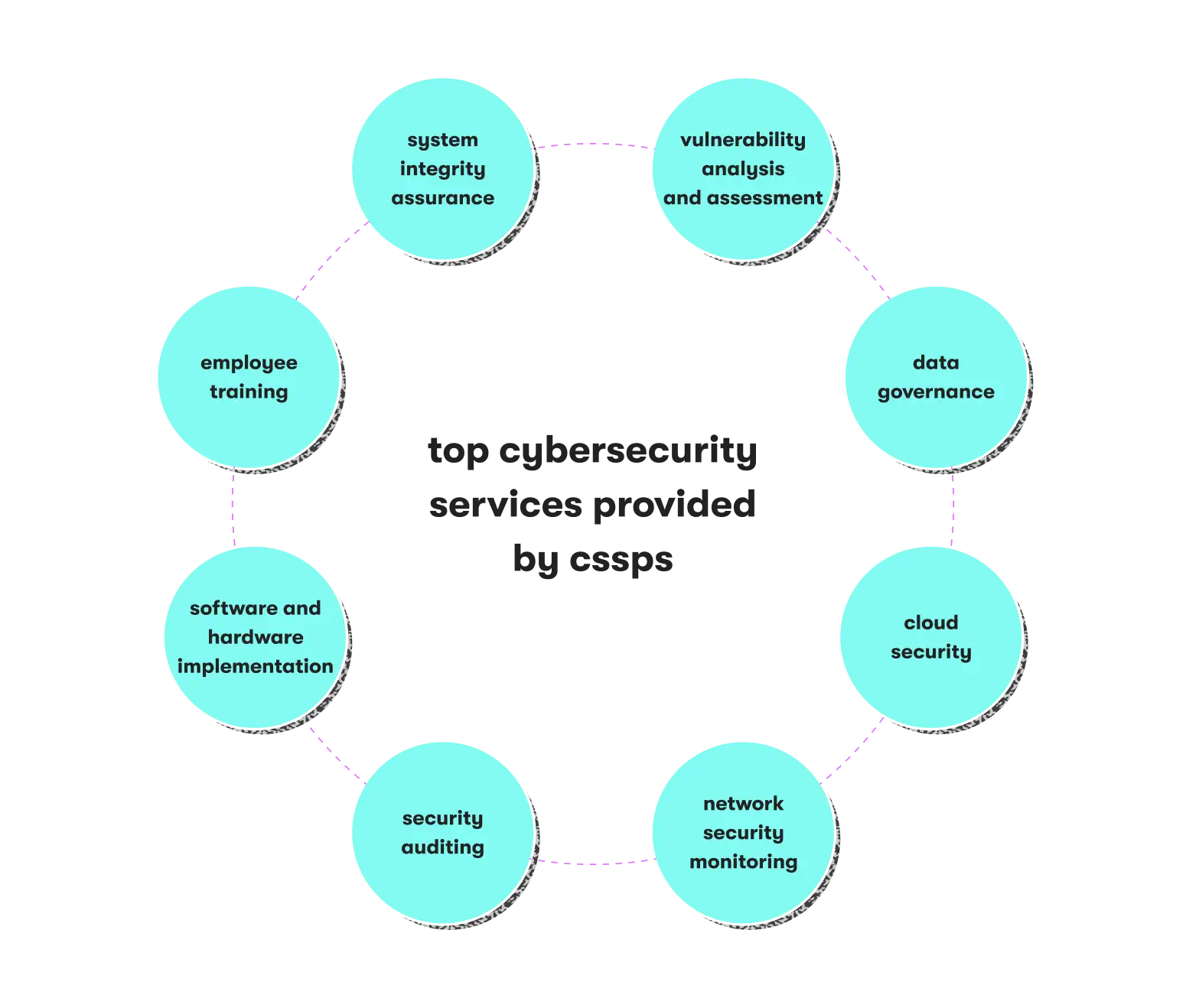
Although offers generally include data governance or cloud network security, services vary from one vendor to another. Currently, the most common services in the market include:
- Vulnerability analysis and assessment
- Data governance
- Cloud security
- Network security monitoring
- Security auditing
- Software and hardware implementation
- Employee training
- System integrity assurance
Opposing the threat: what are the benefits of a CSSP for startups and SMBs?
Small businesses and startups are more vulnerable to cyberattacks compared to big companies. More often than not, they don't have enough resources or expertise to apply solutions such as firewalls or IPS, not to mention the lack of a security operation center (SOC). All these vulnerabilities make them an easy target for cybercriminals.
If data loss occurs, it takes time and money to recover it, in addition to fines, disappointed customers, and reputational losses. The Hiscox Cyber Readiness Report claims that on average, a single attack costs a small U.S. business nearly $25K.
However, with proper security policies in place, businesses can respond to threats beforehand and tackle possible attacks in the future. Again, security is all about satisfied customers. In an increasingly customer-centric world, preventing risks is a much better alternative to losing customers.
In addition, cybersecurity is a matter of constant concern. Businesses evolve, but so do cybercriminals and their arsenal of fraudulent techniques. Thus, partnering with a professional CSSP is a good idea, as you need knowledge and skills that your employees simply don't have.
The benefits of partnering with a CSSP include:
- Getting more expertise. By partnering with a reliable security services provider, startups and SMBs can leverage specialized skills and experience to strengthen their security postures.
- Saving costs. Employing an in-house cybersecurity team, let alone building it from scratch, is costly. By partnering with a CSSP, small companies can avoid the high costs associated with hiring, training, and retaining cybersecurity professionals.
- Staying compliant. Businesses often need to comply with industry-specific regulations and standards related to data protection and privacy. CSSPs ensure your organization meets compliance requirements.
- Focusing on business activities. Partnering with a CSSP allows you to offload the responsibility of managing cybersecurity, enabling you to focus on your core business activities and goals.
GET THESE BENEFITS TODAY
Contact us to learn how our cybersecurity services can enhance your cybersecurity posture so you can focus on business-related activities.
Key CSSP competencies to look for
Your potential CSSP must show relevant expertise to withstand the pressing threats of today. Below are the key CSSP competencies to look for:
- Zero Trust architecture: Zero Trust is a security framework that assumes no trust between users, devices, or networks. This policy emphasizes strict access controls, continuous authentication, and micro-segmentation to protect sensitive data and systems.
- Cloud network security: With the increasing adoption of cloud services, ensuring robust security measures in cloud environments has never been more important. CSSPs put their focus on cloud security strategies, including security configuration management, data encryption, access controls, and cloud infrastructure monitoring.
- Artificial intelligence (AI) and machine learning (ML): AI and ML technologies in cybersecurity can help identify and respond to threats, detect anomalies and malware/ransomware, automate security tasks, and analyze huge amounts of data to identify patterns and potential risks.
- Preventive measures: Cybercriminals use sophisticated techniques to encrypt data and demand ransom payments for its release. Therefore, the focus is on preventive measures like regular backups, network segmentation, employee awareness training, and robust incident response planning.
- Multi-factor authentication (MFA): MFA is becoming more prevalent as a means to enhance login security. The risk of unauthorized access decreases when users provide multiple verification forms (such as passwords, biometrics, or security tokens).
- Threat intelligence and analysis: Threat detection intelligence and analysis is the process of gathering and analyzing information about cyber threats to mitigate risks. Your cybersecurity provider should proactively respond to potential dangers before they can cause significant harm to your company's systems, data, or infrastructure.
How much does cybersecurity as a service cost?
When it comes to pricing, there's no one-size-fits-all model that you can consider a standard. Instead, the costs of cybersecurity services depend on your business's size, specific needs (such as regulatory compliance for different industries, e.g. HIPAA for healthcare), and in-house IT capacity.
Several factors influence the price, including:
- The number of users and connected devices
- The intensity of monitoring
- Additional services
Pricing models also vary. You may be paying per data usage, device, user, or tier pricing. In each case, it’s advisable to contact several providers, explain your needs, get corresponding estimates, and choose a cost-effective option.
It’s true that good cybersecurity as a service won’t come cheap. However, startups and SMBs must understand that cybersecurity saves money in the long run by preventing costly security breaches and mitigating the financial impact of cyber attacks.
How to choose a reliable cybersecurity service provider
Partnering with a reliable cybersecurity service provider is instrumental in making your organization's systems and data safe. Below are the most important factors to consider when choosing a cybersecurity services provider:
- Experience: Consider partnering with cybersecurity providers with strong track records and expertise in cybersecurity. Consider their experience in dealing with similar businesses in your vertical, such as banking or accounting, and their ability to address specific cybersecurity challenges you may face.
- Diversified service offerings: It’s all about the range of services offered by the provider. A broad portfolio of cybersecurity services, including risk assessments, vulnerability management, incident response, penetration testing, security monitoring, and compliance consulting is a good indicator. This ensures they can meet your organization's diverse security needs effectively.
- Certifications and partnerships: Make sure the potential provider has relevant certifications and partnerships with recognized cybersecurity organizations. The Department of Defense (DoD) issues various CSSP certifications to prove the CSSP staff’s competency. Certifications like Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM), as well as partnerships with leading security vendors, indicate the provider’s commitment to high standards.
- Proven security frameworks: Inquire about the provider's security frameworks and methodologies. Look for adherence to industry standards such as ISO 27001, NIST Cybersecurity Framework, or CIS Controls. These frameworks demonstrate that the provider follows established guidelines and employs a structured approach to security.
- Client references and case studies: Request client references or case studies from the provider to understand their past performance. If possible, speak with their existing clients to get insights into their service quality, responsiveness, and ability to deliver results.
DON'T WAIT UNTIL IT'S TOO LATE
Contact us today to learn more about how our cybersecurity services can help safeguard your business and give you peace of mind.
Questions to ask your potential security partner
Let's presume you've shortlisted your potential IT security vendors. What questions should you ask to see the bigger picture? In this part of the article, we'll discuss the questions you should ask your potential security partner.
What technologies do you use?
Although using the latest solutions isn't a silver bullet in itself, staying up to date means that they don't rest on their laurels, so to speak. As mentioned earlier, cyber attacks evolve in real-time, and more and more fraud techniques appear yearly. Thus, using the latest technologies today means you can mitigate risks tomorrow.
What are the possible threats to my business?
Every business differs, and so do cyber threats. Ask your potential cybersecurity service provider about risks posed for your company specifically. Did they have experience working with similar businesses? What are the industry-specific threats? A competent CSSP should enumerate all the possible risks and pinpoint specific weaknesses in your environment.
How experienced is your team?
Like in any other industry, team experience and certifications serve as reliability indicators. Second, it’s about in-depth industry experience. As most businesses operate in highly regulated industries with their own demanding standards, your vendor’s experience in your domain is vital to meet your needs fully.
How fast are your incident response times?
When dealing with security breaches, one can’t underestimate the time factor. Quick reaction during the first hours of intrusion is crucial. Therefore, make sure your potential partner’s team is easy to reach out to on a 24/7 basis.
How do you start with a CSSP?
Hackers get more experienced and tech-savvy by the day — no wonder security incidents hit the headlines all the time. In order to develop an algorithm for countering cyberattacks and intrusion detection, you first need to understand what risks and dangers concern your company.
A security audit is the answer, as this procedure can mitigate the risk of attacks and map out your security environment. A proper cybersecurity audit helps businesses pinpoint current vulnerabilities and realize where their weaknesses are. This way, preventive risk mitigation will keep fraudsters at bay for longer.
However, cybersecurity is an ongoing effort. It makes perfect sense to update your security measures and risk management strategy on a regular basis to adapt to whatever threats online criminals may come up with.
How we can help you
Here at EPAM Startups & SMBs, we offer diversified cybersecurity services based on our hybrid cloud engineering expertise, all-inclusive advisory and implementation services, and future-ready security technologies in our stack.
Check out this project by EPAM and find out how the team provided Genosity with an infrastructure to meet HIPAA requirements with security findings remediations.
Our team of vetted security experts has extensive experience researching and developing effective security solutions that can likewise help protect your business against the latest threats.
TIME IS A CRITICAL FACTOR
When dealing with cybersecurity, time becomes critical. Contact us to find out how we can strengthen your cybersecurity today.
Closing words
In 2022, the cost of a data breach broke a 17-year record and averaged $4.35 million, IBM reports. Regarding such numbers, it's safe to say that cybersecurity as a service is getting more business-critical for companies of all sizes, including startups and SMBs.
Partnering with a reliable cybersecurity service provider is one of the most proactive business decisions you can make today. Therefore, look for a provider that can counter the current and emerging attacks using the latest technologies. We hope you've found this article helpful. Stay safe!

Since 2011, Dmitri has been helping business readers navigate the technology market through expert analysis and editorial work. At EPAM Startups & SMBs, Dmitri shows startups and SMBs across industries how to drive business value from their software engineering investments.
Since 2011, Dmitri has been helping business readers navigate the technology market through expert analysis and editorial work. At EPAM Startups & SMBs, Dmitri shows startups and SMBs across industries how to drive business value from their software engineering investments.
Explore our Editorial Policy to learn more about our standards for content creation.
read more