In this article, you will learn about security in SDLC, its models, key aspects and benefits, and why startups and small and medium-sized businesses (SMBs) should prioritize security in their development processes.
What is security in SDLC?
Security in the software development life cycle (SDLC) encompasses measures and practices to identify, mitigate, and prevent software security vulnerabilities throughout development stages. The secure SDLC addresses security concerns from the very beginning, whether as part of cybersecurity services or as part of the accepted software engineering practices.
A secure software development lifecycle involves integrating security testing and other activities into an existing development process. The process typically consists of several phases, including requirements gathering, design, coding, testing, and maintenance. Integrating security at each phase helps ensure the software is resilient to potential cyberattacks and malware.
The challenge
To put it simply, a secure SDLC is integral because it places security at the core of software development right from the start. Nevertheless, many small businesses fall behind in incorporating security into their software development life cycle.
It's not unusual that development teams view security as an obstacle, considering it a challenge that necessitates revisiting code they believed was complete. This mindset slows down both the overall development process and new feature implementation.
Therefore, your team must prioritize security integration by establishing secure software processes that empower, rather than hinder, the creation of robust products. With that being said, let's dive into the topic and analyze the secure SDLC's key aspects, models, and benefits.
Key aspects of the secure SDLC
From understanding user needs to testing, these key aspects define the journey from the product’s inception to implementation.
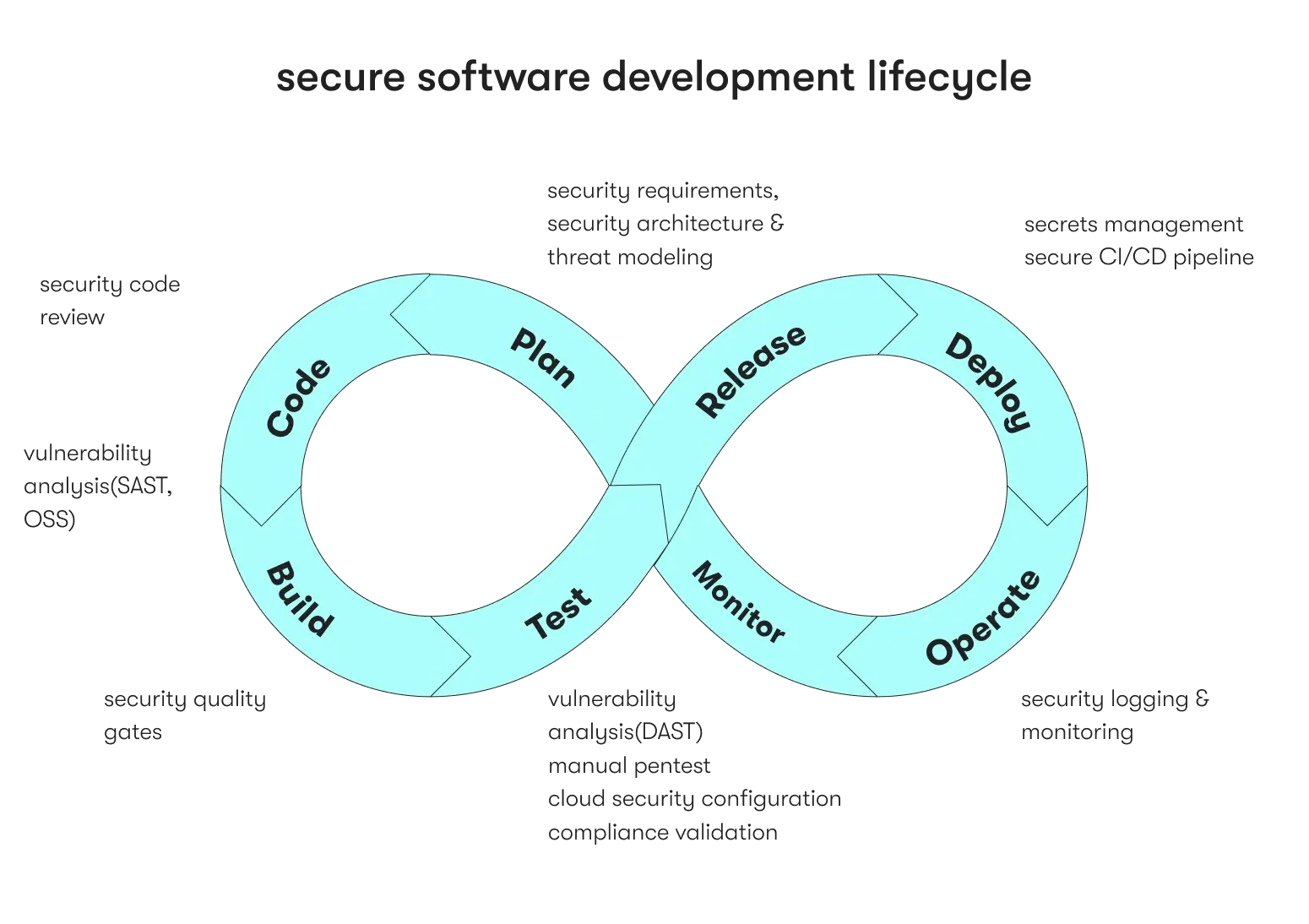
- Threat modeling and risk assessment: Identifying potential threats and vulnerabilities that could affect the software and assessing the associated cybersecurity risks. This practice helps in prioritizing measures based on the level of risk.
- Secure design: Developing a secure architecture and design for the software, considering such principles as least privilege, data minimization, and proper access controls.
- Secure coding practices: Writing code that is protected from common security vulnerabilities like SQL injections, cross-site scripting (XSS), and buffer overflows. These practices involve following coding guidelines, input validation, and output encoding.
- Static and dynamic code analysis: Conducting static code analysis to identify vulnerabilities in the source code and dynamic analysis to test the software while it's running for potential security flaws.
- Security testing: Performing security activities, including penetration testing and vulnerability scanning, to identify and fix possible weaknesses and vulnerabilities.
- Security documentation: Creating documentation outlining security requirements, design decisions, and risk assessment to maintain consistency throughout development.
- Training and awareness: Ensuring that development teams are well-trained in security best practices and aware of common security risks.
- Ongoing monitoring and maintenance: Continuously monitoring the software in production to identify and address emerging security vulnerabilities.
- Incident response planning: Having a plan that helps address incidents and sensitive data breaches effectively, minimizing their impact on the software and users.
PLACE SECURITY AT THE CORE OF YOUR SOFTWARE DEVELOPMENT PROCESS
Fundamental SDLC models
There are several SDLC models, each with its own approach to organizing the stages of software development. Let’s analyze some of the most popular secure development models your team may use.
- Waterfall: The waterfall model follows a linear and sequential approach, where each phase of the SDLC is completed before moving on to the next. The model includes phases like requirements analysis, design, implementation, testing, deployment, and maintenance. Once a phase is completed, it is not revisited, and some teams may find it limiting in regard to future changes.
- V-model (validation and verification model): The V-model extends the waterfall model by emphasizing testing at each stage of development. Every development phase has a corresponding testing phase, forming a "V" shape. This approach helps ensure the software is thoroughly tested and validated before deployment.
- Agile: Agile is an iterative and incremental approach that emphasizes flexibility and collaboration and involves breaking down the development process into smaller iterations or sprints. Teams carry out phases iteratively, leaving room for frequent adjustments based on feedback.
- Scrum: Scrum is a specific framework within the Agile methodology, including three roles: Product Owner, Scrum Master, and Development Team. Development occurs in time-boxed iterations called sprints, usually lasting 2–4 weeks. The team sets priorities from a product backlog and delivers a potentially shippable product increment at the end of each sprint.
- Kanban: Kanban is another Agile framework that visualizes the workflow and limits work in progress. The framework aims to improve efficiency by continuously optimizing the flow of work items through the development process.
- CI/CD: This model includes a set of practices and processes within software development that aims to automate and streamline the building, testing, and deployment of software applications. The goal of the CI/CD approach is to ensure that software changes can be quickly and reliably integrated into the main codebase and deployed to production environments with minimal manual intervention.
- Iterative model: With this model, development work is first conducted based on clearly defined requirements and features are later added through iterations until the system is complete. This approach is meant to break down a development project into smaller chunks.
- Spiral model: The spiral model combines iterative development with elements of risk assessment, repeating a series of cycles, each focusing on identifying and addressing potential risks. This model is particularly suitable for projects where risk management is a high priority.
- RAD (rapid application development): RAD is focused on quickly developing prototypes and involves iterative development. This approach is particularly useful for projects with well-defined requirements and a need for rapid development.
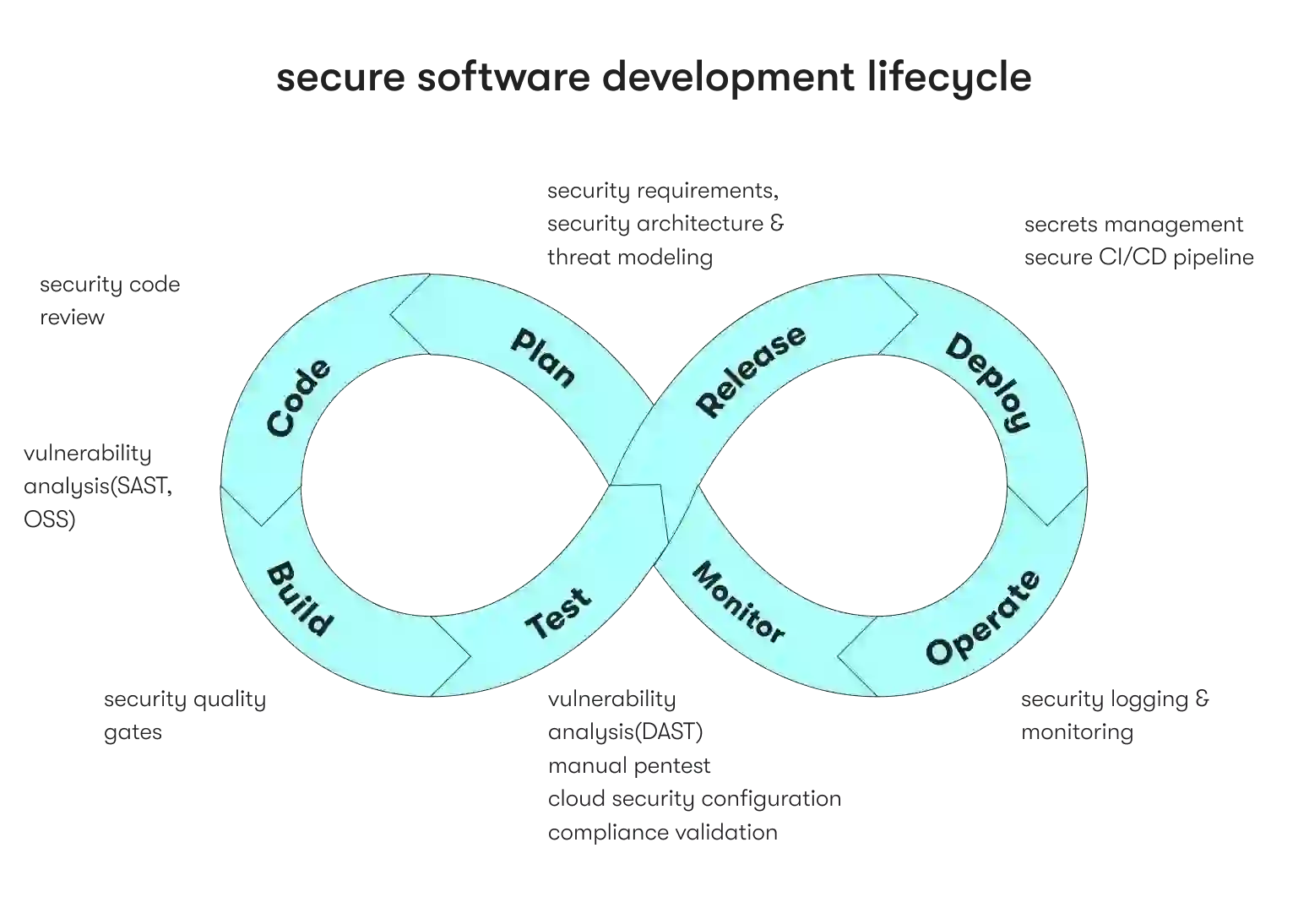
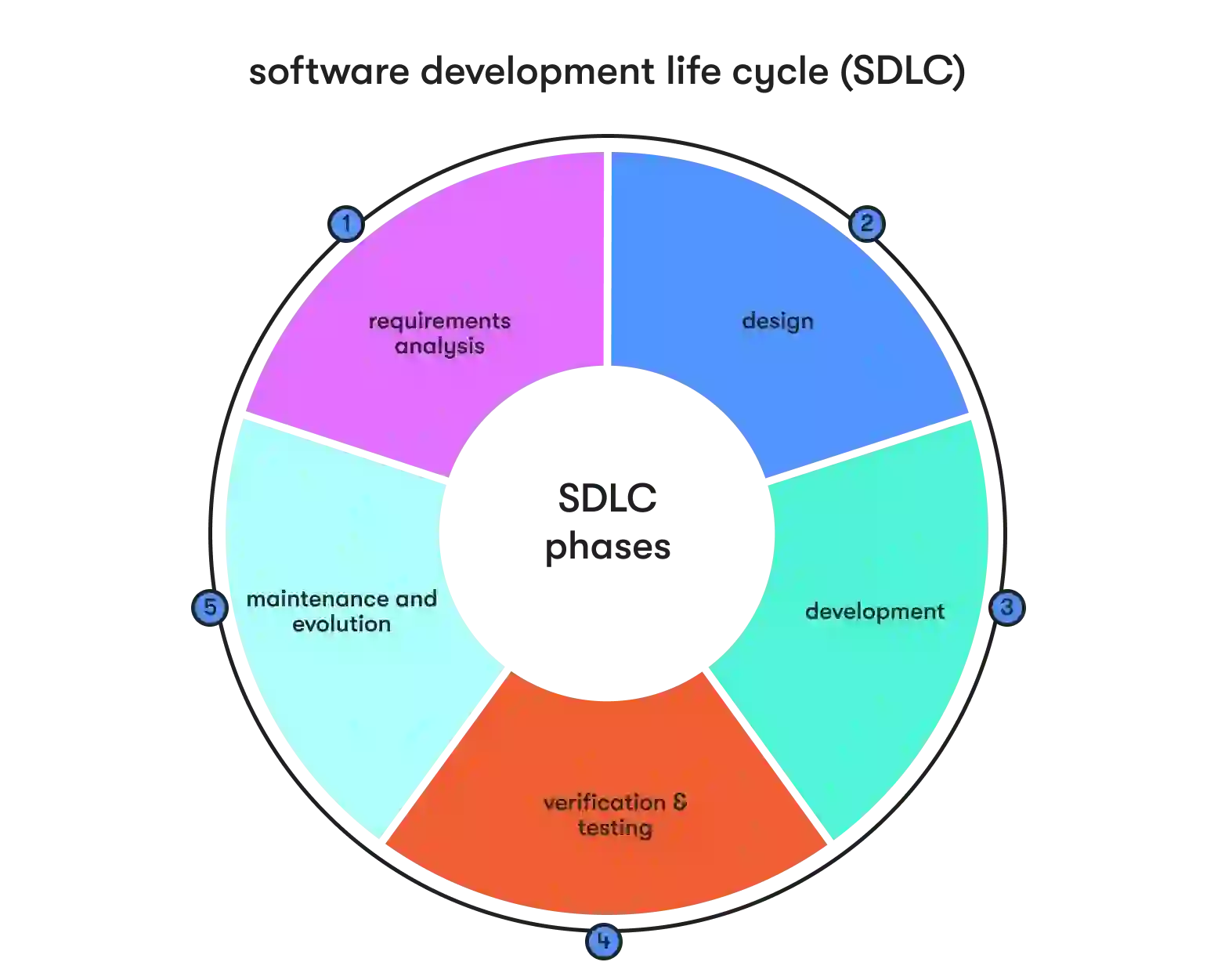
The secure SDLC phases
The software development life cycle (SDLC) serves as the roadmap guiding the creation of software solutions and outlines a series of interconnected phases that drive a project from its inception to deployment.
Each phase is pivotal in ensuring the software's successful development, testing, and implementation and meeting the project's unique needs and objectives. In this section, we will delve into the intricacies of these SDLC phases when it comes to security, examining how they streamline the development process and deliver software that aligns with user requirements.
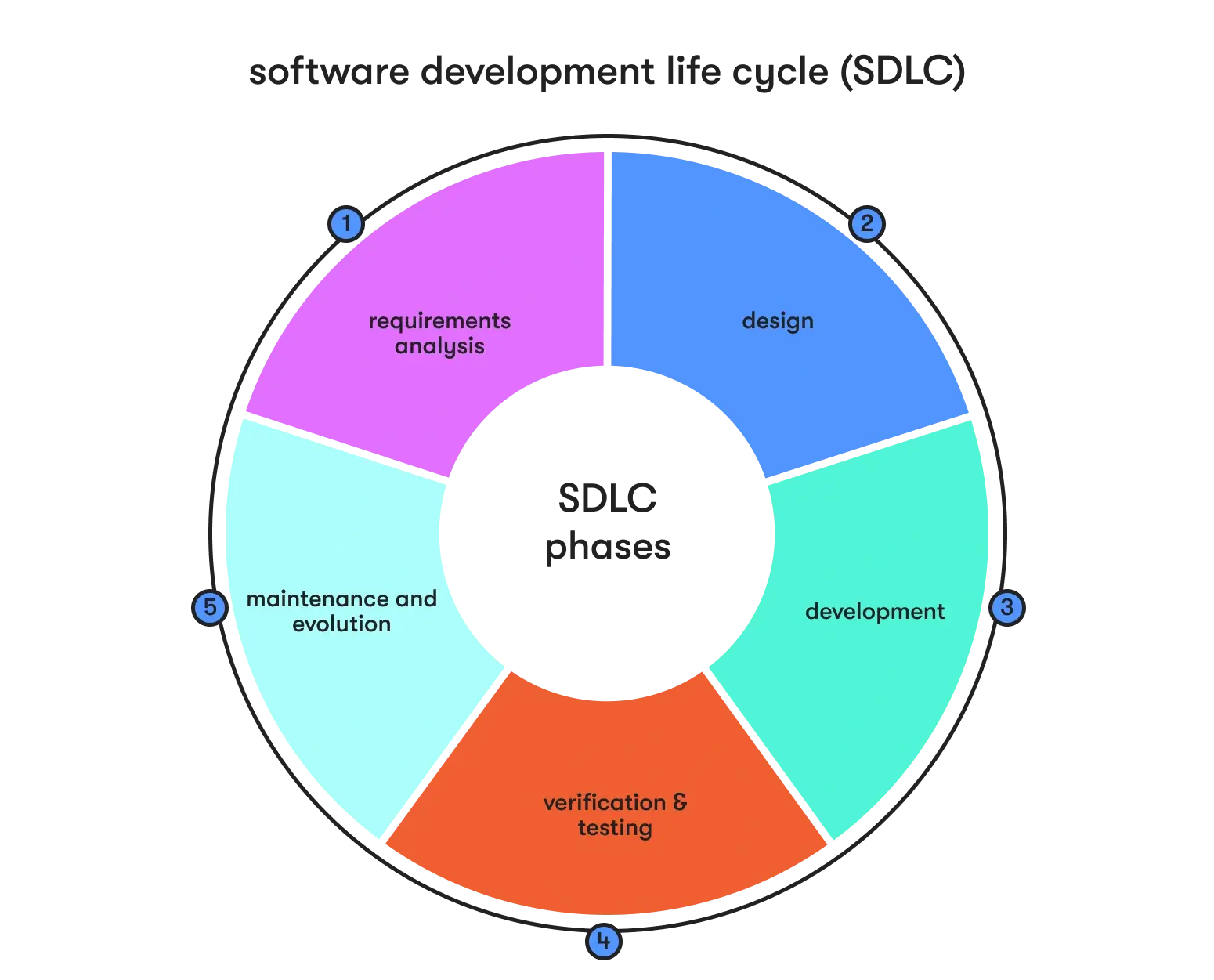
Phase 1. Requirements analysis
The team collects requirements for new features from various stakeholders. At this stage, identifying any security considerations related to the functional requirements gathered for the upcoming release is crucial.
Phase 2. Designing
In this phase, the requirements within the scope are translated into an elaborated plan for their implementation in the actual application. Functional requirements typically outline what actions should occur, while security requirements emphasize what actions should be avoided.
Phase 3. Development
At this step, the focus shifts to ensuring the code is well-written from a security perspective. Secure coding guidelines are usually established, and the team conducts code reviews to verify adherence to these guidelines. These reviews can be either manual or automated, using techniques like static application security testing (SAST).
However, in modern application development, the responsibility extends beyond writing code. For instance, most applications today rely on existing functionality provided by open-source components. These components facilitate the rapid delivery of new features. In fact, over 90% of deployed applications consist of these open-source elements. They are typically assessed using software composition analysis (SCA) tools.
Secure coding standards in this context might include:
- Utilizing parameterized, read-only SQL queries to retrieve data from the database, reducing the risk of queries being misused
- Validating user inputs before processing the enclosed data
- Sanitizing any data returned from the database before showing it to the user
- Assessing open-source libraries for vulnerabilities before incorporating them
Phase 4. Verification and testing
The verification phase involves comprehensive testing to ensure alignment with the initial design and requirements. At this stage, the team incorporates automated security testing through various technologies. Automated tools like CI/CD pipelines are often used to manage verification and release.
Verification in this phase might include:
- Automated tests that demonstrate critical pathways within the application
- Automatic execution of application unit tests that verify the correctness of the underlying code
- Dynamic incorporation of application secrets via automated deployment tools in a production setting
Phase 5. Maintenance and evolution
The product journey doesn't conclude with the application release. In fact, vulnerabilities might surface long after the release, in the code developed by the team or increasingly within the underlying open-source components. This trend results in more "zero-day" vulnerabilities — previously undiscovered issues revealed in production by maintainers.
Addressing these vulnerabilities necessitates the development team to patch the software, which might even entail substantial rewriting of application functionality. Vulnerabilities at this stage could also stem from external penetration tests by ethical hackers or submissions via "bug bounty" programs. Dealing with these production-related issues requires careful planning and integration into future releases.
HIRE OUR SECURITY TEAM TO DELIVER A FUTURE-READY SOLUTION
SDLC technologies and tools
SDLC technologies and tools refer to the software, applications, platforms, and resources used throughout the software development life cycle to facilitate various stages of development, testing, deployment, and maintenance.
Static application security testing (SAST): SAST tools analyze an application's source code or compiled code to identify vulnerabilities and security flaws early in the development process.
- Examples: Checkmarx, Fortify, SonarQube
Dynamic application security testing (DAST): DAST tools simulate attacks against a running application to identify vulnerabilities from an external perspective. They provide insights into how an application responds to various threats.
- Examples: OWASP ZAP, Burp Suite, Acunetix
Interactive application security testing (IAST): IAST tools combine elements of SAST and DAST. They analyze the code and observe the application during runtime to identify vulnerabilities, providing more accurate results.
- Examples: Contrast Security, Hdiv Security
Software composition analysis (SCA): SCA tools scan the open-source components used in an application to identify known vulnerabilities and manage third-party software risks.
- Examples: WhiteSource, Black Duck, Snyk
Secure code review tools: These tools assist developers in manually reviewing code to identify vulnerabilities and adherence to coding security standards.
- Examples: CodeSonar, Crucible, Review Board
Code analysis tools: These tools analyze the codebase for potential security issues, performance bottlenecks, and code quality concerns.
- Examples: SonarQube, ESLint, PMD
Web application firewalls (WAF): WAFs protect applications by filtering and monitoring incoming traffic. They can detect and block malicious requests, providing an additional layer of security.
- Examples: ModSecurity, Imperva WAF, Cloudflare WAF
Vulnerability scanning tools: These tools scan systems and applications for known vulnerabilities, helping businesses stay up to date with the latest security patches.
- Examples: Nessus, OpenVAS, Qualys
Continuous integration/continuous deployment (CI/CD) pipelines: Integrating security checks within CI/CD pipelines ensures that security assessments are automatically performed as part of the development process.
- Examples: Jenkins, GitLab CI/CD, Travis CI
Secure design tools: These tools assist in designing secure architecture and making informed security decisions during the design phase.
- Examples: Microsoft Threat Modeling Tool, OWASP Application Security Verification Standard
These technologies and tools, when integrated into the SDLC, help identify vulnerabilities early, ensure secure coding practices, and enhance the overall security posture of the software. It's essential to choose the tools that best align with your company's development practices and security requirements. In this regard, finding a reliable cybersecurity partner is a good choice, especially for growing businesses.
The benefits of the secure SDLC
The secure SDLC offers a structured framework that helps businesses create high-quality software systematically and efficiently. The framework can be tailored to fit both small projects with limited resources and large enterprise-level projects.
This approach leads to improved project management, better collaboration, reduced risks, and increased client satisfaction. Here are some more of the key benefits of following the secure SDLC approach:
- Structured process: Provide your team with a well-defined and organized process for developing software. The SDLC breaks down the complex task of software development into manageable phases and activities, making the process more predictable and manageable.
- Quality assurance: Emphasize testing and validation at each phase, ensuring that the software is tested for bugs, functionality, security vulnerabilities, and performance.
- Clear communication: Encourage clear communication among team members, stakeholders, and clients. The documentation and defined processes help everyone understand project goals, requirements, and progress.
- Efficient resource allocation: Prevent overloading certain phases and ensure a balanced distribution of effort throughout the project. With predefined phases and tasks, the SDLC helps in allocating resources effectively.
- Change management: Manage changes by incorporating them into specific phases, ensuring that the impact on the project is assessed and controlled.
- Predictable timelines: Break down development into phases and set milestones. The SDLC contributes to more accurate time estimations and project scheduling.
- Documentation: Encourage the creation of documentation at each stage, including requirements, design specifications, test cases, and user manuals. This documentation serves as a valuable resource for maintenance, troubleshooting, and future enhancements.
- Continuous improvement: Many SDLC models promote iterative development and learning from each phase. This practice guarantees continuous improvement, incorporating feedback and insights from previous iterations.
- Compliance and security: SDLC models with a focus on security incorporate practices throughout the development process, ensuring that security concerns are addressed from the outset.
How do you get started?
Below are actionable steps that you can take to advance toward a safe software development life cycle and bolster your company's security posture:
- Enhance knowledge. Foster an environment of awareness by educating colleagues about optimal secure coding practices while also acquainting yourselves with existing security frameworks.
- Use technology to collect user feedback. Employing technology to gather user feedback is essential, particularly for projects involving extensive user interactions. Diligently review the feedback form submissions and address users' specific challenges.
- Promote collaborative practices. Nurturing collaboration is a core principle of the SDLC. Engage your technical leads in business analysis meetings to discuss prototypes and business functionalities. This level of involvement ensures that developers are well-informed about tasks they might encounter down the line.
- Initiate architecture risk analysis. At the project's inception, engage in architecture risk analysis to identify potential vulnerabilities. This proactive approach aids in addressing security concerns right from the start.
- Utilize code scanning tools. Harness the power of code scanning tools for a multifaceted approach to security, including static analysis, dynamic analysis, and interactive application security testing. Such tools provide a comprehensive evaluation of your codebase for potential vulnerabilities.
By embracing these actionable strategies, you'll be on your way to cultivating a secure SDLC that safeguards your business' digital assets and bolsters its resilience against cyber threats.
Final words
Cybersecurity services are on the rise. Surely, the transition away from the traditional software development life cycle paradigm takes time and demands a shift in your team’s mindset. It all boils down to selecting and implementing an appropriate SDLC model. Yet, each project stands distinct, and there's no such thing as a universal process model in software engineering.
Scrutinizing the primary software life cycle models alongside their merits, drawbacks, and contextual applications helps you make an informed choice. Nevertheless, each methodology has inherent limitations, and you might need to adapt the model to your project, not vice versa.
Ensuring a secure software development process is integral to a product's success, and prioritizing project requisites over methodologies emerges as a pivotal tenet. This practice often entails a fusion of multiple SDLC models or even the creation of a new one.
FAQ

Since 2011, Dmitri has been helping business readers navigate the technology market through expert analysis and editorial work. At EPAM Startups & SMBs, Dmitri shows startups and SMBs across industries how to drive business value from their software engineering investments.
Since 2011, Dmitri has been helping business readers navigate the technology market through expert analysis and editorial work. At EPAM Startups & SMBs, Dmitri shows startups and SMBs across industries how to drive business value from their software engineering investments.
Explore our Editorial Policy to learn more about our standards for content creation.
read more