Understanding the intricacies of penetration testing and calculating its costs is a priority when requesting cybersecurity services.
Penetration testing, often called "pen test" or “pentest,” is a fundamental practice for assessing the security of your digital assets. From your web applications to your network infrastructure, penetration testing involves meticulously examining vulnerabilities that may remain hidden. The average cost of a penetration test can vary depending on several factors, and understanding the methodology behind pricing is crucial for organizations aiming to bolster their security posture.
Penetration testing services encompass various testing types, each serving a unique purpose. From the dynamic assessment of web apps in web application penetration testing to the comprehensive scrutiny of network security in network penetration testing, the diversity of testing methodologies allows for tailored evaluations of an organization's vulnerabilities.
These penetration testing types adhere to specific guidelines and industry standards, such as PCI DSS (Payment Card Industry Data Security Standard), ensuring that your organization meets compliance requirements.
In this article, we'll explore the intricacies of penetration testing pricing, delve into the various certifications and qualifications of penetration testers, and provide insight into what influences the cost of penetration tests. Whether you seek to protect your organization from potential vulnerabilities or validate your security posture, understanding penetration testing costs is the first step toward comprehensive cybersecurity and guarding against data breaches and cyberattacks.
What is a penetration test?
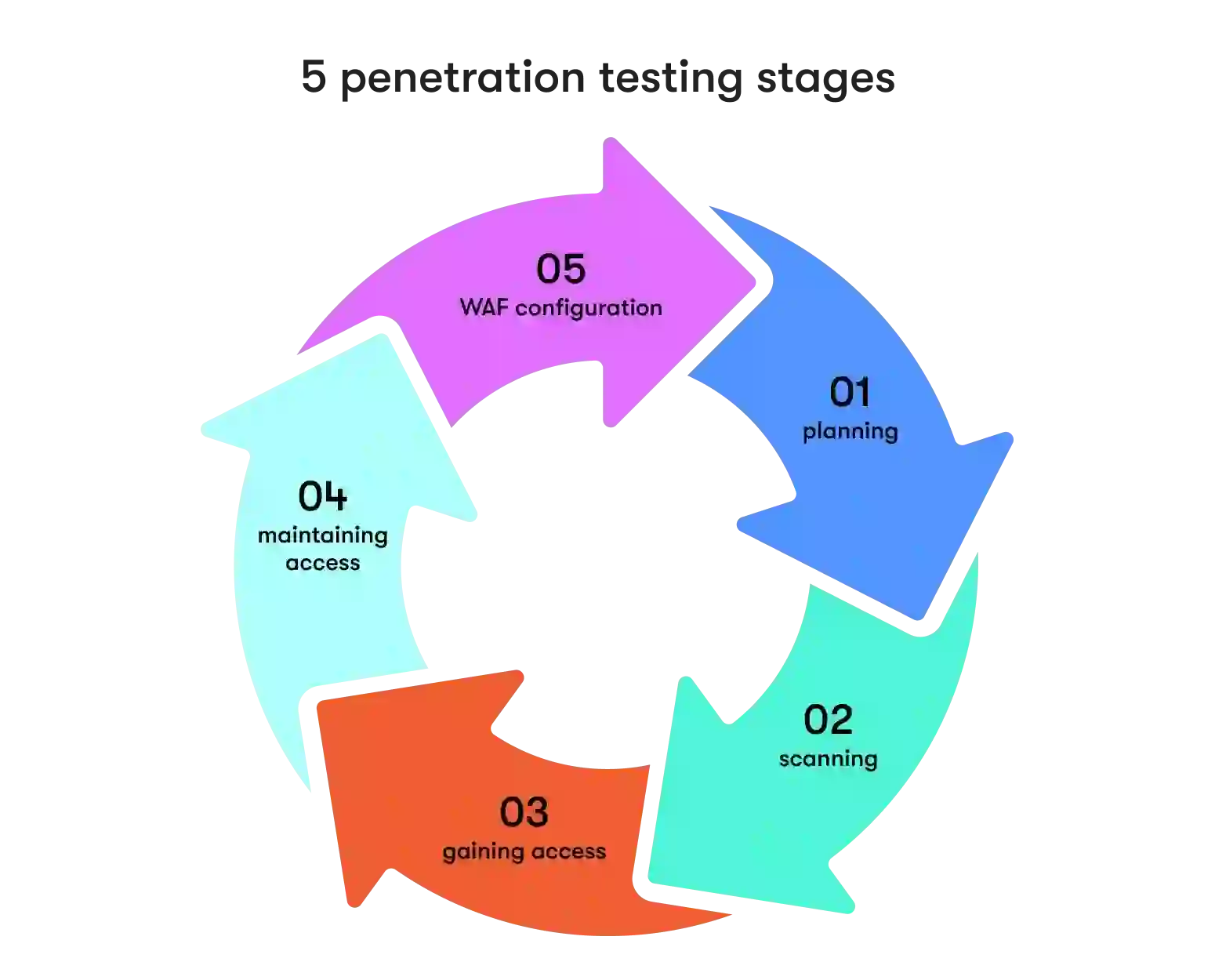
A penetration test is a meticulous exploration of your digital infrastructure aimed at unearthing vulnerabilities that malicious actors could exploit. This proactive approach serves as a cybersecurity safety net, allowing you to uncover and rectify security weaknesses before cybercriminals capitalize on them. Penetration testing is a complex process but can be narrowed down to 5 main stages.
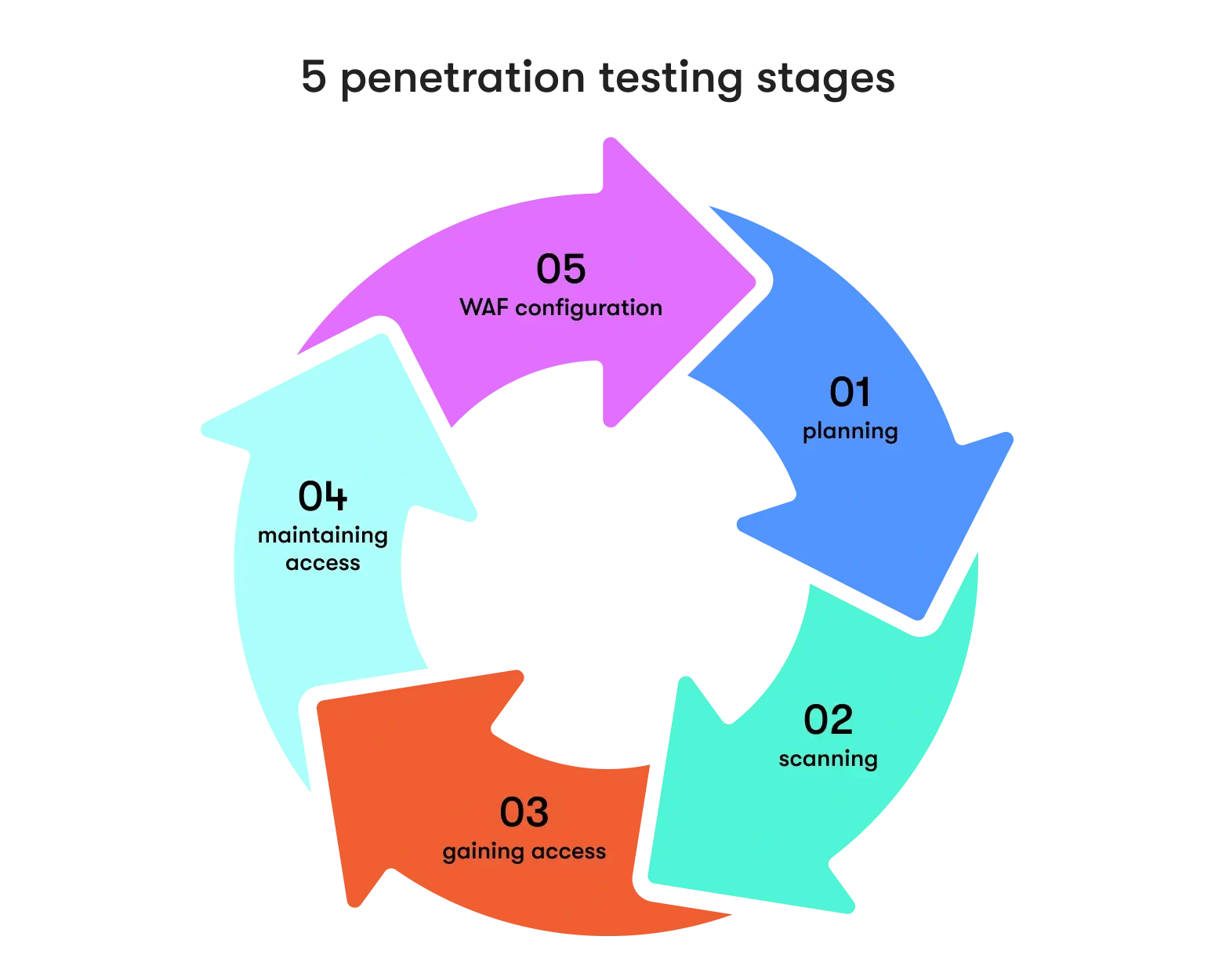
- Planning
First, test goals are defined and information is gathered to ensure the guidelines and processes are transparent. Without this foundation, pentests can’t be run or will be ineffective against threats.
- Scanning
The scanning stage involves using specialized tools to analyze how a target system or network responds to intrusion attempts. It's a critical phase where vulnerabilities are identified and weaknesses are exposed.
- Gaining access
This penetration testing stage involves attempting to gain unauthorized access to a system or network. It mimics the tactics employed by potential attackers to identify vulnerabilities that could be exploited.
- Maintaining access
Once initial access is gained, the penetration tester maintains that access. This step replicates scenarios where attackers attempt to remain undetected within a system or network.
- WAF configuration
Web Application Firewall (WAF) configuration is the final stage that focuses on ensuring the WAF is appropriately configured to protect against common web application attacks.
Why is a pen test important?
The importance of penetration testing cannot be overstated. It simulates real-world cyberattacks, enabling you to understand where your vulnerabilities lie and how to bolster your defenses. With regular pen testing, your organization can avoid data breaches, financial losses, and damage to its reputation. Keeping your software safe is the foundation of a successful operation.
What can pen tests identify?
Penetration testing is your cybersecurity ally in uncovering vulnerabilities across your digital landscape. It serves as a reality check, identifying potential entry points that cybercriminals could exploit. In straightforward terms, it answers a range of critical questions:
Where would a hacker target you?
Think of penetration tests as a guided tour for hackers. Pen tests spotlight weak access controls, unpatched software, misconfigured systems, and other vulnerabilities within your digital realm, areas that attackers could hone in on.
How would an attacker target you?
Penetration tests leave no room for guesswork. “Red teams” engaged in offensive cybersecurity simulate an arsenal of real-world attack techniques, from attempting unauthorized access to executing malicious code and exploiting known vulnerabilities. This simulation provides a litmus test for your network's resilience.
How would your defenses fare against an attacker?
The tests scrutinize your security controls with a discerning eye. They evaluate your organization's ability to detect, respond, and repel threats. The aim is to ensure your defenses are battle-ready, not just theoretical constructs.
What would the potential severity be if a breach were to occur?
Penetration testing offers a sobering glimpse into the potential aftermath of a security breach. It allows you to gauge the potential damage to your organization's reputation and bottom line. This realism is crucial for risk management and proactive security measures.
SECURE YOUR BUSINESS TODAY WITH OUR PENETRATION TESTING COMPANY
Enhance your cybersecurity defenses with our experts, discover vulnerabilities, and strengthen your protection with comprehensive testing reports.
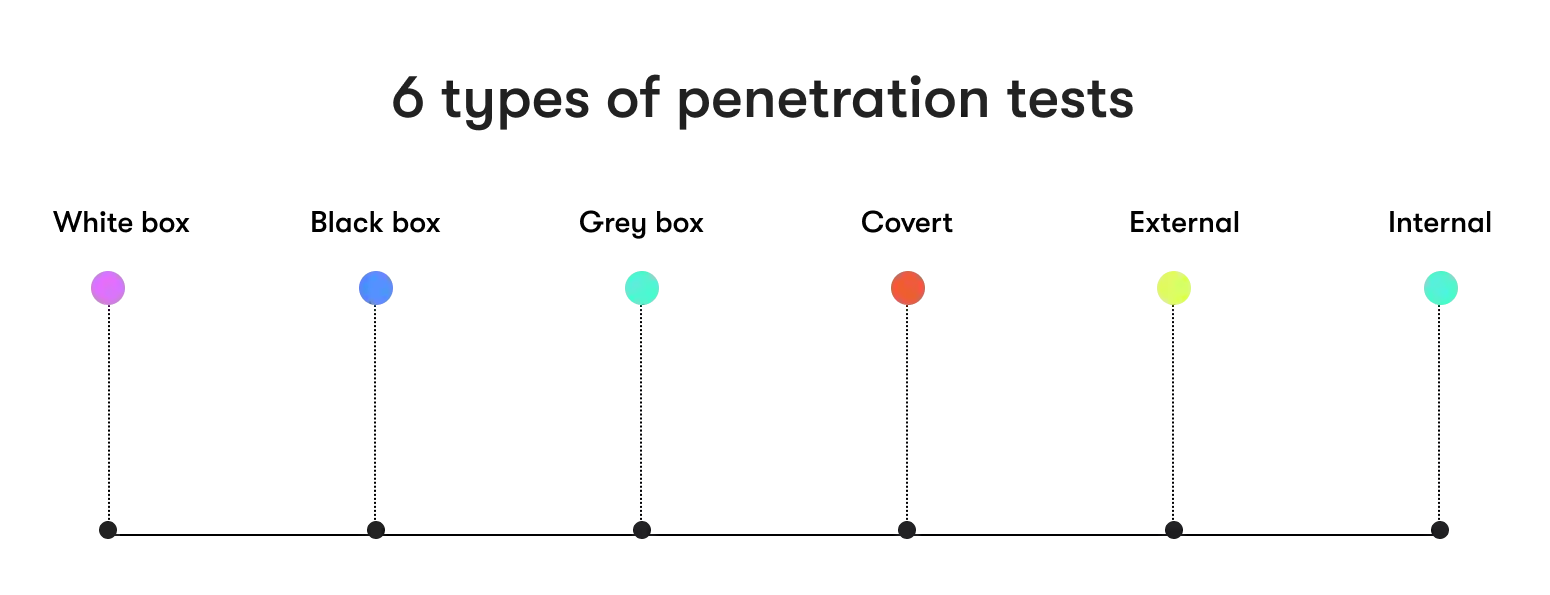
Types of pen tests
Penetration tests are anything but one-size-fits-all. They are a versatile toolkit of vulnerability assessments, each carefully tailored to meet specific needs and address distinct scenarios. To truly appreciate the depth and breadth of penetration testing, let's delve into the distinct types of penetration tests.
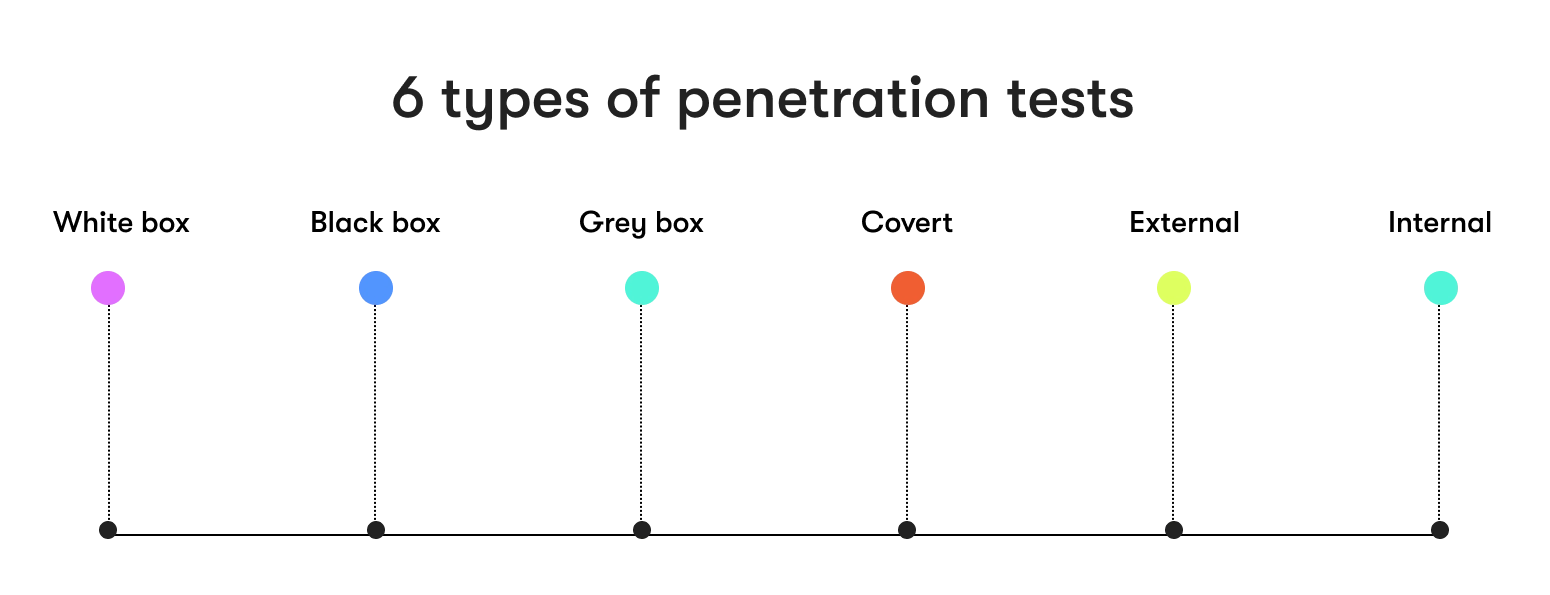
White box penetration tests
In the world of penetration testing, the white box pentesting approach stands as a beacon of transparency. These tests are conducted with a profound understanding of your system, allowing for an extensive and candid examination of your digital infrastructure. The straightforward nature of white box testing unveils vulnerabilities and evaluates your defenses with utmost clarity.
Black box penetration tests
On the other end of the spectrum, the black box pentesting simulates an attack by an external threat without prior knowledge of your system. These tests authentically assess your organization's readiness for unanticipated attacks. While the approach may appear optimistic, it is firmly rooted in the unpredictability of real-world threats.
Grey box penetration tests
Grey box tests occupy the confident middle ground. They strike an equilibrium between white and black box testing, showcasing adaptability to various scenarios and engagement levels. The confidence in this approach lies in its versatility, offering insights into your network's security without revealing every detail.
Covert penetration tests
Covert tests present authoritative simulations of a determined attacker's tactics. They provide valuable insights into how your organization would fare against a stealthy intrusion. The authority of this approach lies in its ability to uncover vulnerabilities that might go unnoticed in other tests, effectively mirroring the strategies of a genuine attacker.
External penetration tests
External tests focus on vulnerabilities that exist beyond your network perimeter. They scrutinize elements like your website, cloud services, and remote access points, offering a no-nonsense assessment of your digital presence's frontline defense.
Internal penetration tests
Internal tests turn the spotlight inward, assessing your network from within. They focus on vulnerabilities that employees or insiders could exploit. These tests adopt an optimistic approach by evaluating your in-house operations and shoring up defenses against potential insider threats.
How much does penetration testing cost?
As you’ll see below, penetration testing can cost anything between $2,000 and $50,000+ depending on multiple factors. The penetration test cost is not arbitrary; it reflects the investment needed to secure your digital assets confidently and authoritatively. Understanding the factors that influence cost empowers organizations to make informed decisions and fortify their cybersecurity defenses.
- Company size: The size of your organization plays a significant role in determining the cost of a penetration test. Larger organizations boasting intricate infrastructures may require more extensive testing to evaluate the depth and breadth of their digital defenses. This can influence the cost, but it's also an optimistic investment in safeguarding valuable digital assets.
- Scope and complexity: A comprehensive security assessment encompassing a broad range of systems and applications demands more resources, time, and expertise. This confident approach to testing ensures that every nook and cranny of your digital ecosystem is scrutinized, but it also factors into the overall pricing.
- Number of live IP addresses: Every live IP address within the scope of a penetration test contributes to its complexity. An authoritative assessment must account for each IP address, considering the potential vulnerabilities lurking behind each one. This meticulous examination of IP addresses underscores the comprehensive nature of the test and the investment required.
- Methodology: The chosen methodology carries its weight when determining the cost of a penetration test. For example, automated vulnerability scanning and manual testing come with varying costs. The straight-talking reality is that the selected methodology shapes the test's depth and thoroughness, which inevitably impacts the price.
- The goals of the test: What you aim to achieve with the test directly influences the cost. Whether uncovering vulnerabilities, enhancing security, or meeting compliance requirements, specific objectives come with optimistic investments to fulfill these goals.
- Type of test: The type of test you opt for, be it white, black, grey, or covert, carries its pricing structure. A confident choice in selecting the appropriate test type aligns with your security objectives and strategic planning, but it also comes with associated costs that match the chosen approach.
- Type of applications: Testing aspects of your digital landscape, such as web applications, mobile applications, or network infrastructure, can have distinct costs. An authoritative approach ensures that every facet of your digital presence is thoroughly examined, but it also accounts for the variations in pricing.
- Data sensitivity: Highly sensitive data requires a more stringent, straight-talking testing approach. Protecting sensitive information is paramount, requiring a more comprehensive and rigorous assessment, which naturally influences the overall cost of the penetration test.
Penetration testing pricing examples
Web application testing
Web app testing is a cybersecurity service identifying vulnerabilities and weaknesses in web-based applications and websites. It involves thoroughly assessing the application's security, including its authentication mechanisms, input validation, and protection against common attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Pricing example: The cost for web application testing can range from $2,000 to $50,000 or more, depending on the complexity and size of the application. A simple web application with standard features might be on the lower end of the scale. In contrast, a highly complex ecommerce site or a web application handling sensitive customer data might require a more comprehensive test and, therefore, a higher price.
Сloud testing
Cloud testing involves assessing the security of an organization's cloud infrastructure, including platforms like AWS, Azure, Google Cloud, or other cloud service providers. It aims to identify misconfigurations, vulnerabilities, and access control issues that could expose an organization to cloud-based threats.
Pricing example: The cost of cloud testing can vary from $5,000 to $50,000 or more, depending on the scale and complexity of the cloud environment. A small to medium-sized organization with a single cloud service may require a basic-level assessment. At the same time, a large enterprise with a complex multi-cloud setup will necessitate a more comprehensive and, therefore, more expensive evaluation.
SaaS
SaaS testing is focused on assessing software-as-a-service security. This type of software can include customer relationship management (CRM) applications, project management, or other business functions. The testing aims to identify vulnerabilities and configuration issues within a SaaS platform.
Pricing example: SaaS testing costs typically range from $2,000 to $20,000 or more, depending on the SaaS application's complexity and testing depth. Basic SaaS applications with limited features may be at the lower end of the pricing scale. At the same time, more complex, enterprise-level SaaS solutions will require a more comprehensive assessment and, therefore, a higher price.
How often do you need to carry out pentesting?
The frequency of penetration testing hinges on various factors, including changes in your network, applications, and the evolving threat landscape. Regular security testing is essential to ensure your digital assets' ongoing security and integrity.
Bottom line
In conclusion, penetration testing is critical to a high-quality cybersecurity strategy. A comprehensive understanding of the average pen testing cost and its importance equips you to make informed decisions in safeguarding your digital assets and protecting your organization from potential threats. Our experienced penetration testing team is ready to assist you in assessing and enhancing your cybersecurity measures.

Anush has a history of planning and executing digital communications strategies with a focus on technology partnerships, tech buying advice for small companies, and remote team collaboration insights. At EPAM Startups & SMBs, Anush works closely with subject matter experts to share first-hand expertise on making software engineering collaboration a success for all parties involved.
Anush has a history of planning and executing digital communications strategies with a focus on technology partnerships, tech buying advice for small companies, and remote team collaboration insights. At EPAM Startups & SMBs, Anush works closely with subject matter experts to share first-hand expertise on making software engineering collaboration a success for all parties involved.
Explore our Editorial Policy to learn more about our standards for content creation.
read more